Bitwarden - Architecting software for security
Introduction
Bitwarden strives to build a safe and secure password manager that everyone can use1. In our previous posts, we have discussed this vision, how it translates to software design decisions and to the code base of the project. This week we want to lay the focus on the security of the Bitwarden project. As a password manager security is a key component of the Bitwarden product.
Users trust the encryption utilized by Bitwarden as well as the company with all of their logins or files. In this essay, we will discuss the main security features Bitwarden offers. The architectural decisions they have made in regards to security. The secure code they offer, and how they distribute this safely. Finally we will delve into the steps Bitwarden takes to deny attackers or malicious users exploits in their system.
Main security features
In this section, we want to offer the reader a short overview of the main security features Bitwarden offers.
Secure user data
The initial one we want to discuss is the security of user specific data. A user can save files, passwords and notes with Bitwarden and expect Bitwarden to not be able to access this information. In their privacy policy2 Bitwarden states that they cannot access this data due to a Zero Knowledge Architecture (in a zero knowledge architecture the application only stores encrypted data, this is further explained in architecture for security section). User data Bitwarden does use is personal data to be able to offer the Bitwarden service such as e-mail addresses, payment information and name.
Secure data collaboration
Bitwarden can further this claim to ensure private data collaboration for users. To do so you can use the built-in organization structure. By linking user data to an organization, a user can link other users to that organization to ensure a secure manner of exchanging and collaboration on files or passwords. By offering this service employers who have purchased the enterprise edition can expect their employees to utilize this secure manner of data sharing.
Password generator
The main feature offered by the password manager is the password generator. This feature can generate a strong password of random characters up to a length of 128 characters. The addition of capital letters, punctuation and numbers to the pool can easily be chosen by the user. To ensure the zero knowledge architecture the password generator runs on the client side. This means the database of Bitwarden is never in contact with your password in the form of plaintext. Therefore the password generator Bitwarden utilizes has to be re-built on every platform. Once the user saves the generated password, it is encrypted and passed on to the Bitwarden (or self-hosting) server.
Architecture for security
Zero knowledge architecture
To ensure good data security, Bitwarden decided to use a Zero Knowledge Architecture3. The concept of Zero-Knowledge Architecture at its simplest is any approach that allows someone or something to verify a set of data (aka ‘knowledge’) so it can be used for a particular purpose without providing the service visibility to the set of data itself. Not only are passwords stored encrypted on Bitwarden servers, they are never decrypted anywhere in the backend system. All sensitive information is only ever decrypted on a client where a user is logged in, as the master password is the only key to access the items within the vault. The decryption and encryption happens on the client-side, which means that only encrypted data is transmitted and stored on the Bitwarden server. This is known as End-to-End encryption. 4 This way Bitwarden doesn’t have access to the content of the vault, and have zero knowledge of its contents.
This architecture can be seen in the Figure below 1.
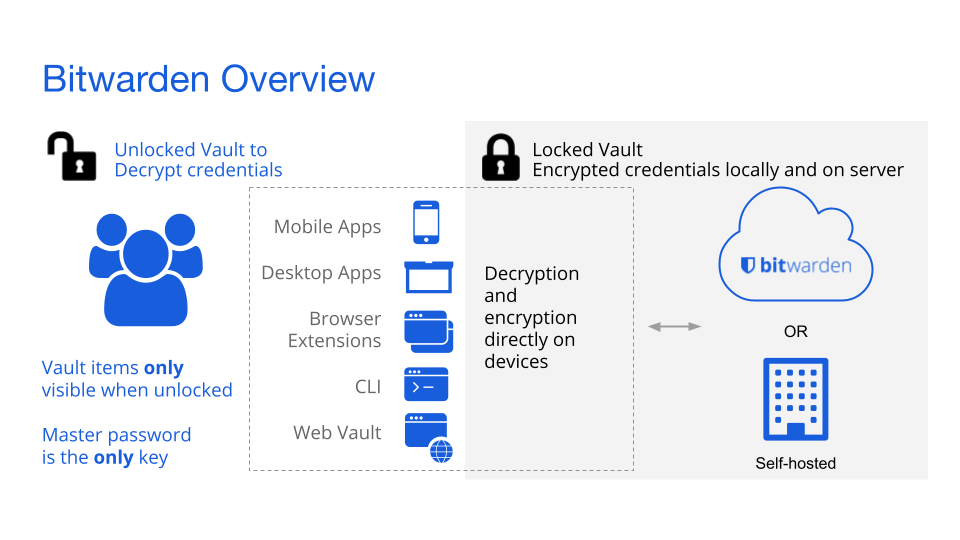
Figure: Bitwarden zero knowledge encryption Architecture
Open source
The transparent architecture of Bitwarden contributes greatly to its security 5. Bitwarden’s two main architectural decisions on its security model are “don’t invent your own crypto”, and “work conform industry standards” 1. The transparent open-source architecture of Bitwarden contributes to both of these design goals by using the power of the community and pre-existing cryptography methods, to prevent the need for inventing their own cryptography methods. Furthermore, because of the transparency, Bitwarden’s features and infrastructure security are vetted and improved by their global community.
Security by design
When designing cryptography algorithms, two routes can be taken. Security by design or security through obscurity. Security by design means that the security of the method depends on the good design of the encryption algorithm. If the algorithm would be known by an attacker, it would still be secure. In fact, often the algorithms used are publicly available. Security through obscurity is the opposite and depends on the secrecy of the algorithm. If the algorithm is discovered, all encrypted items are instantly no longer protected, and the encryption is worthless. By using the transparent architecture described above, Bitwarden’s security is based on design, not obscurity.
Two factor authentication
When a malicious user would obtain the master password of a Bitwarden account, this user has access to all passwords stored in that Bitwarden account. To secure a Bitwarden account better, Bitwarden advises users to enable two factor authentication. However, this is not mandatory, nor is it enabled by default.
Two-factor authentication uses, like the name implies, another factor for authenticating, besides the password of a user. This second factor can be, for example, clicking a confirmation link in an email, SMS, or notification in a smartphone app. Only having the master password is then no longer enough to gain access to an account, but access to the victim’s email account or smartphone is now also required.
Coding for security
To achieve security for its users, Bitwarden’s security starts in their code where everything is done to ensure that every bit of the product is secured against the highest of security standards.
Third party security audits
It is not only in its code that Bitwarden values transparency, the same goes for its security. In November of 2018 Bitwarden contacted a reputable third party, security firm Cure53. Cure53 tested everything in the Bitwarden ecosystem from clients to API’s and even the hosting platform 6. They were able to find five vulnerabilities of which only one required immediate attention. Bitwarden found this to be a very positive result given the size and complexity of the bitwarden project.
Bitwarden is committed to regular security audits on various aspects of the Bitwarden platform. In the summer of 2020, Bitwarden released their Bitwarden Network Security Assessment Report, in which auditing firm Insight Risk Consulting performed a security assessment and penetration test7. Again the complete Bitwarden ecosystem was examined and the results were even better than last time. Only two issues of moderate severity were highlighted.
Bitwarden has obtained Certifications SOC 2 Type 2 and SOC 3. System and Organization Controls (SOC) comprise a set of control frameworks that independent auditors use to validate and certify an organization’s systems and policies with respect to security and data protection. The purpose of SOC standards is to provide confidence and peace of mind for organizations when they engage third-party vendors. A SOC-certified organization has been audited by an independent certified public accountant who determined the firm has the appropriate SOC safeguards and procedures in place 8.
By being pro-active in seeking third party audits and transparent in sharing their results, Bitwarden hopes to prove their commitment to security and integrity and further strengthen the trust of their users. This is certainly the case with us, as of now two of our 4 group members make use of Bitwarden for its features, security and above all, transparency.
Secure handling of code
A product is only as secure as its weakest link, is not a saying, but it does hold for Bitwarden. That is why the communication between the Bitwarden code has to be secure as well as the hosting infrastructure. For communication between codebases, Bitwarden utilizes the secure connection HTTPS. These codebases themselves are hosted on secure cloud servers of Microsoft Azure Cloud and backed by the Microsoft team 9. Microsoft is a renowned name in the software industry, however, if users still do not trust them, Bitwarden is open-source and offers the capability to self-host.
Testing
To ensure the continuation of security through code, the quality and correctness of the code has to be maintained. This is done through code testing, which is mainly implemented in the back-end. Due to the secure design using Zero Knowledge Architecture and secure communication, this is the only area where testing is crucial to secure operation of Bitwarden. This is done thoroughly and has been audited by third parties and no remarks were made on this aspect.
Distribution for security
Hosting and Deployment
The system architecture of Bitwarden consists of multiple separately runnable units. Where the client applications are installed by the users and distributed by Bitwarden. The server application, which is mainly responsible for saving the data, consists of multiple separate runnable/deployable units itself. This application can be self-hosted by companies or by Bitwarden and is distributed as a docker image on the docker hub of Bitwarden. The other application can be downloaded from the site of Bitwarden.
As explained in the deploy guide of Bitwarden the application can be deployed by using a container orchestration tool.10
These container orchestration tools can be run on an own server of the company or by a cloud service provider.
Most container orchestration tools have features that make configuring security easier.
For example Kubernetes11 has an insightful guide to use the security option in different IaaS Providers.
Companies can even choose to make the self-hosted Bitwarden system only available on their own network, making accessing the vault even harder for malicious users.
Although this sounds more secure than using the Bitwarden hosting for your companies vault data, this may be not true. Bitwarden uses the Azure cloud services for their hosting.12 Microsoft is one of the big cloud services provides and has high-security standards. The point here is that went a company self-hosts their Bitwarden server there is a higher chance of misconfiguring the hosting or deployment procedures. This could mean a greater chance of security issues.
The database of the system can be hosted in the same cloud or server. The Azure SQL service Bitwarden uses has its own security features as well and can be read here.13
Fault tolerance
If a system is highly fault-tolerant the system can still properly operate in the event of a failure of one of its components. As the server consists of a few separated containers, each component could be deployed with redundancy. When a component fails the copies of the same part, can distribute a part of the load. This improves both fault tolerance and availability.
Bitwarden against attacks/exploits
The final thing we want to touch upon is how Bitwarden approaches security issues in their code base. As an open-source project anyone can create a pull request. But these are reviewed and can only be merged by developers with write access. Each repository of the Bitwarden project offers a SECURITY.md14 which users can access to report issues but also white-hat hackers can read to inform Bitwarden of potential vulnerabilities.
To tie into this white-hat approach Bitwarden has also offered bounties on the website hackerone 15. This is a website where people can offer vulnerabilities and the enterprise developers keep a close eye on the posts here.
Conclusion
After having done this thorough analysis and attending the Bitwarden Vault hours of March 2021, we are all convinced that Bitwarden is as secure and integrous as they claim to be. Having seen the way they communicate their work and plans with the community and the effort put into interaction, we believe that the team behind Bitwarden is really committed to their product and firmly believe that they are on the right path to a truly great open-source secure and integrous password manager. The only thing that rests is convincing Erik and Daan to join the Bitwarden community and leave the Google password manager behind.
References
-
Spearrin, K., Marshal, A., & Orenstein, G. (2020, August 20). Building a zero knowledge architecture[Slides]. Crowdcast. https://www.crowdcast.io/e/zero-knowledge-architecture ↩︎
-
Bitwarden. (n.d.-c). Privacy Policy | Bitwarden. Bitwarden Privacy Policy. Retrieved March 26, 2021, from https://bitwarden.com/privacy ↩︎
-
Orenstein, G. (2020b, August 6). How End-to-End Encryption Paves the Way for Zero Knowledge. Bitwarden Blog. https://bitwarden.com/blog/post/end-to-end-encryption-and-zero-knowledge/ ↩︎
-
Orenstein, G. (2020, June 13). Vault Security in the Bitwarden Password Manager. Bitwarden Blog. https://bitwarden.com/blog/post/vault-security-bitwarden-password-manager ↩︎
-
Bitwarden. (n.d.-c). Open Source Software | Bitwarden. Bitwarden Open Source Software. Retrieved March 26, 2021, from https://bitwarden.com/open-source/ ↩︎
-
Cure53. (2018, November). Bitwarden Security Assessment Report. https://cdn.bitwarden.com/misc/Bitwarden%20Security%20Assessment%20Report.pdf ↩︎
-
Insight Risk Consulting. (2020, July). Bitwarden Network Security Assessment Report. https://cdn.bitwarden.com/misc/Bitwarden%20Network%20Security%20Assessment%20Report%20-%202020.pdf ↩︎
-
Spearrin, K. (2020, August 25). Bitwarden achieves SOC 2 certification. Bitwarden. https://bitwarden.com/blog/post/bitwarden-achieves-soc-2-certification/ ↩︎
-
Bitwarden. (n.d.-d). Storage. Retrieved March 29, 2021, from https://bitwarden.com/help/article/data-storage/ ↩︎
-
Bitwarden. (n.d.). Bitwarden - Install on permise. Bitwarden Help. Retrieved March 29, 2021, from https://bitwarden.com/help/article/install-on-premise/ ↩︎
-
Kubernetes. (2021, February 11). Overview of Cloud Native Security. https://kubernetes.io/docs/concepts/security/overview/ ↩︎
-
Azure Security. (n.d.). Microsoft Azure. Retrieved March 29, 2021, from https://azure.microsoft.com/en-us/overview/security/ ↩︎
-
J. (2020c, October 26). Security Overview - Azure SQL Database & Azure SQL Managed Instance. Microsoft Docs. https://docs.microsoft.com/en-us/azure/azure-sql/database/security-overview ↩︎
-
Spearrin, K. (2018, February 27). Bitwarden server SECURITY.md. GitHub. https://github.com/bitwarden/server/blob/master/SECURITY.md ↩︎
-
Bitwarden. (n.d.-c). HackerOne - Bitwarden. HackerOne. Retrieved March 26, 2021, from https://hackerone.com/bitwarden/hacktivity?type=team ↩︎